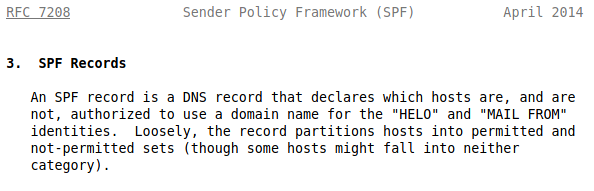
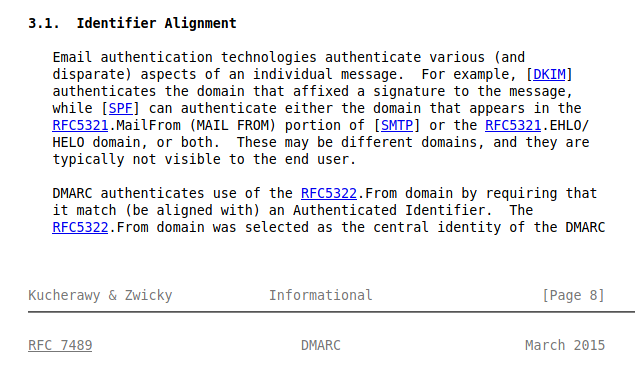
Something I have realised recently is that SPF does not give a damn about the From of an email. SPF checks the HELO/EHLO and MAIL FROM.
So, if you've published a SPF record (no DMARC/DKIM) for your domain are you protected from attackers spoofing From @ mydomain .com? 👇
No. An attacker can just set up or compromise a server for which there is a passing SPF record. For example they compromise hacked .com which publishes this SPF
v=spf1 mx a ~all
They can now send with HELO/MAIL FROM of hacked .com.
They send a phishing campaing with From @ mydomain .com and MAIL FROM @ hacked .com (say webmaster @ hacked .com).
The receiving server (let's say Microsoft) will check SPF against the MAIL FROM. And since the record contains "a" it will be a SPF pass.
Microsoft will gladly accept the e-mail. They may flag it and put it in junk but it won't be due to SPF failing.
The victim will receive the mail and it will look like it came from some address @ mydomain .com.
Your SPF record for mydomain .com had no say in this process.
So how do you prevent this kind of spoofing? You have to use DMARC, which will perform additional checks based on the actual From address.